When it comes to PCI compliance, merchants can’t afford to treat security as a single layer.
Today’s threats—from zero-day exploits to real-time script tampering—move faster than ever. And while external vulnerability scanning (ASV) remains foundational to PCI DSS, the rise of client-side attacks has introduced a new frontier of risk: the browser.
So let’s be clear: It’s not ASV vs. script monitoring.
It’s ASV and script monitoring. Together.
Here’s why both are essential, and how they protect your business in different, complementary ways.
What Is ASV Scanning?
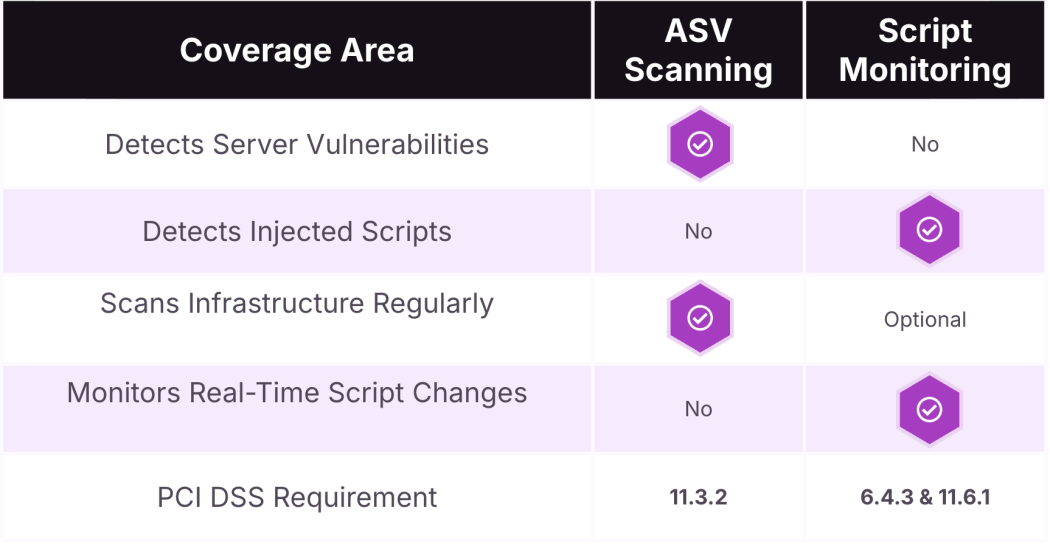
ASV scanning refers to the external vulnerability scans required under PCI DSS Requirement 11.3.2. These scans must be conducted at least quarterly and performed by a PCI SSC–approved scanning vendor (ASV). The term “ASV” technically refers to the vendor—not the scan itself—but the two are often used interchangeably. Regardless of naming, this requirement has long served as one of the most established and critical components of PCI compliance, helping organizations identify internet-facing vulnerabilities before attackers do.
At Aperia Compliance, our ASV scanning service is trusted by thousands of merchants and processors to detect and report vulnerabilities in their internet-facing infrastructure.
An ASV scan checks for:
Known vulnerabilities like XSS, SQLi, and remote code execution
Misconfigured services or firewall gaps
Weak TLS configurations and exposed ports
Backdoors, malware, and outdated server software
If your cardholder data environment is connected to the public internet in any way, you need ASV scanning. Full stop.
It’s a core part of the PCI ecosystem… and it’s not going anywhere.
But Here's the Problem: It’s Not Built for the Browser
What ASV scanning does brilliantly is uncover externally visible risks, from the outside in.
But what it doesn’t do (and wasn’t designed to do) is monitor live scripts running inside a consumer’s browser. And that’s exactly where modern attackers are striking.
Think of a merchant’s checkout page: full of JavaScript delivered from CDNs, third-party services, payment libraries, and marketing tools. All of it renders inside the browser. None of it is visible to the server.
When one of those third-party scripts is compromised, like the chatbot plugin in the Ticketmaster breach, data can be siphoned off instantly, without any alert or trace on the server.
ASV scanning might eventually detect malware or domain issues. But the attack will already be in motion.
That’s where script monitoring comes in.
Script Monitoring: Built for Modern Threats
PCI DSS 4.0 introduced two new requirements—6.4.3 and 11.6.1—specifically to address this gap.
Requirement 6.4.3: Maintain an inventory of all scripts on payment pages and verify each is authorized.
Requirement 11.6.1: Detect and alert on unauthorized changes to content and scripts on payment pages.
Script monitoring does both.
It builds a real-time baseline of every script a merchant loads in their checkout flow, whether it’s embedded directly or sourced from a third-party provider. It then continuously checks for changes, unauthorized additions, or signs of tampering.
If something unexpected appears—an extra line of obfuscated code, a malicious domain injection, or a version mismatch—alerts fire immediately. Compliance teams know before the breach becomes a headline.
It’s fast, silent, and accurate. And it’s exactly the kind of proactive defense PCI DSS 4.0 was built to enforce.
Why You Need Both
ASV scanning and script monitoring don’t compete—they complete each other.
ASV scanning defends the edge. Script monitoring defends the browser. Together, they create a layered, modern PCI compliance strategy:
So instead of choosing between them, smart acquirers and processors are adopting both.
Why?
Because attackers aren’t picking one route. They’re using every path available.
Don’t Wait for a Breach to Bridge the Gap
Digital skimming isn’t theoretical. It’s real, active, and targeting businesses daily.
If a script is injected at 10 a.m. and your quarterly ASV scan isn’t scheduled until next month, that’s 30+ days of silent data theft—unless you’ve got script monitoring in place.
With layered controls from Aperia Compliance, you’re not only meeting the letter of PCI DSS 4.0—you're fulfilling the original intents of the standards: proactivity, prevention, and a customer-first approach.
Ready to see how ASV scanning and continuous script monitoring work together? Schedule a walkthrough with our compliance team.